¶ Introduction
GPO (Group Policy Object) is a tool for Windows system administrators that enables centralized management of operating system configuration and running applications on multiple computers at the same time. In other words, the GPO allows you to define rules about what computers and their users can do. The configuration of these rules takes place on the server and then, using a special filtering mechanism, it is sent to selected computers.
Distribution of certificates via GPO is a remote and automatic upload of certificates to all devices belonging to a given group of objects or administrative unit (so-called auto-enrollment). The use of this certificate management method also allows for automatic certificates renewal. Solutions of this type are appreciated by administrators, as they significantly improve and accelerate the process of distributing certificates and other elements that enhance network security.
¶ How to distribute certificates via GPO?
It can be done in a few following steps
¶ 1. The users' certificates
1.1. Open Active Directory Administrative Center on the server with ability to manage the domain.
1.2. In a place of your choice create a security group. To do this, right-click and select New > Group. The users who belong to this group will participate in so-called auto-enrollment.
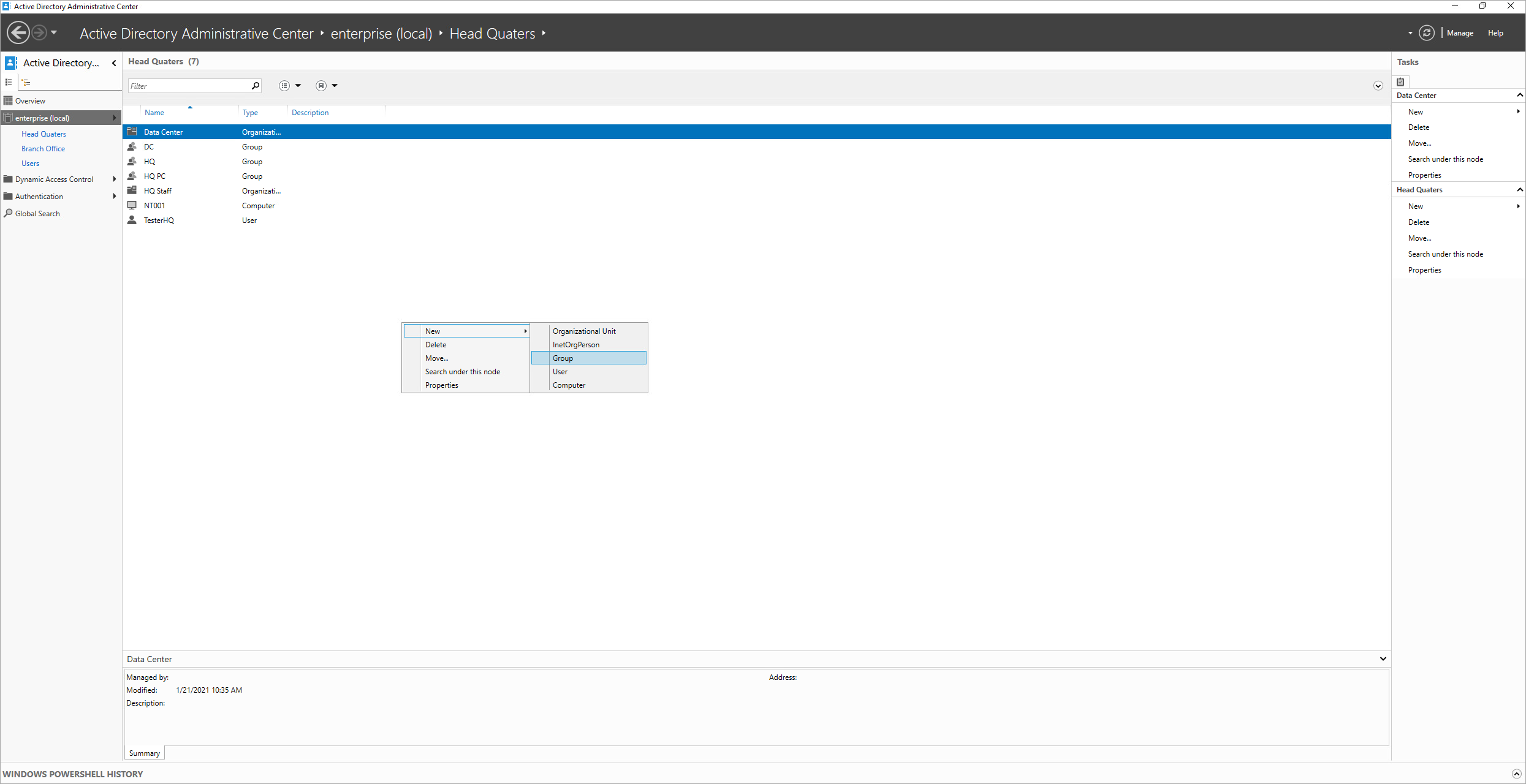
1.3. Enter your user group (e.g. Auto Enrollment User). save it with OK.
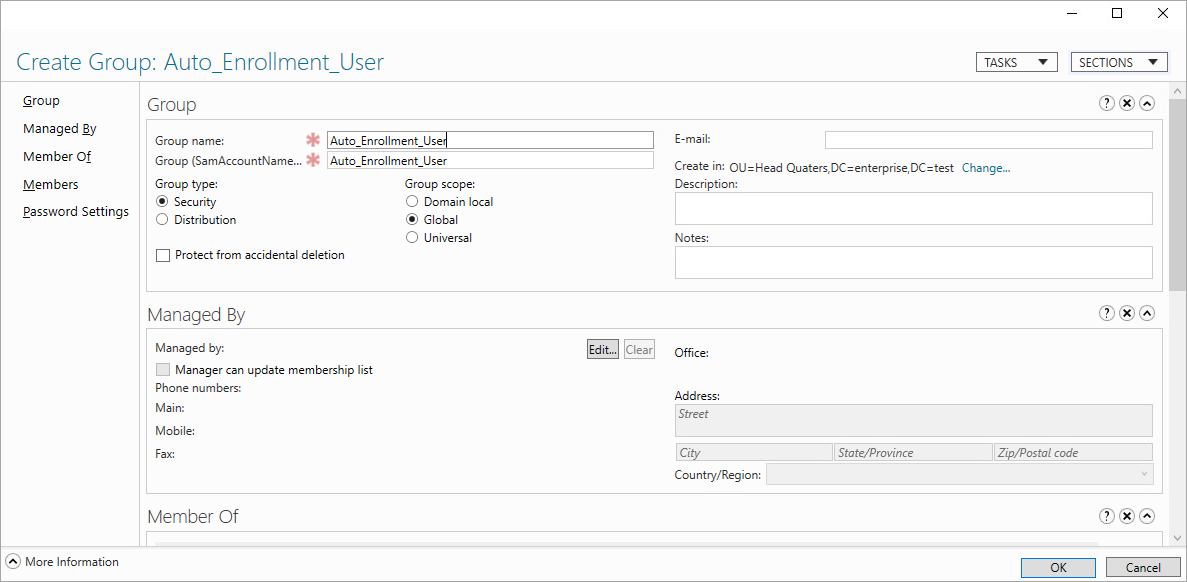
1.4. Add users to the group you have just created. To do this, right-click on the selected user and select: Add to group…
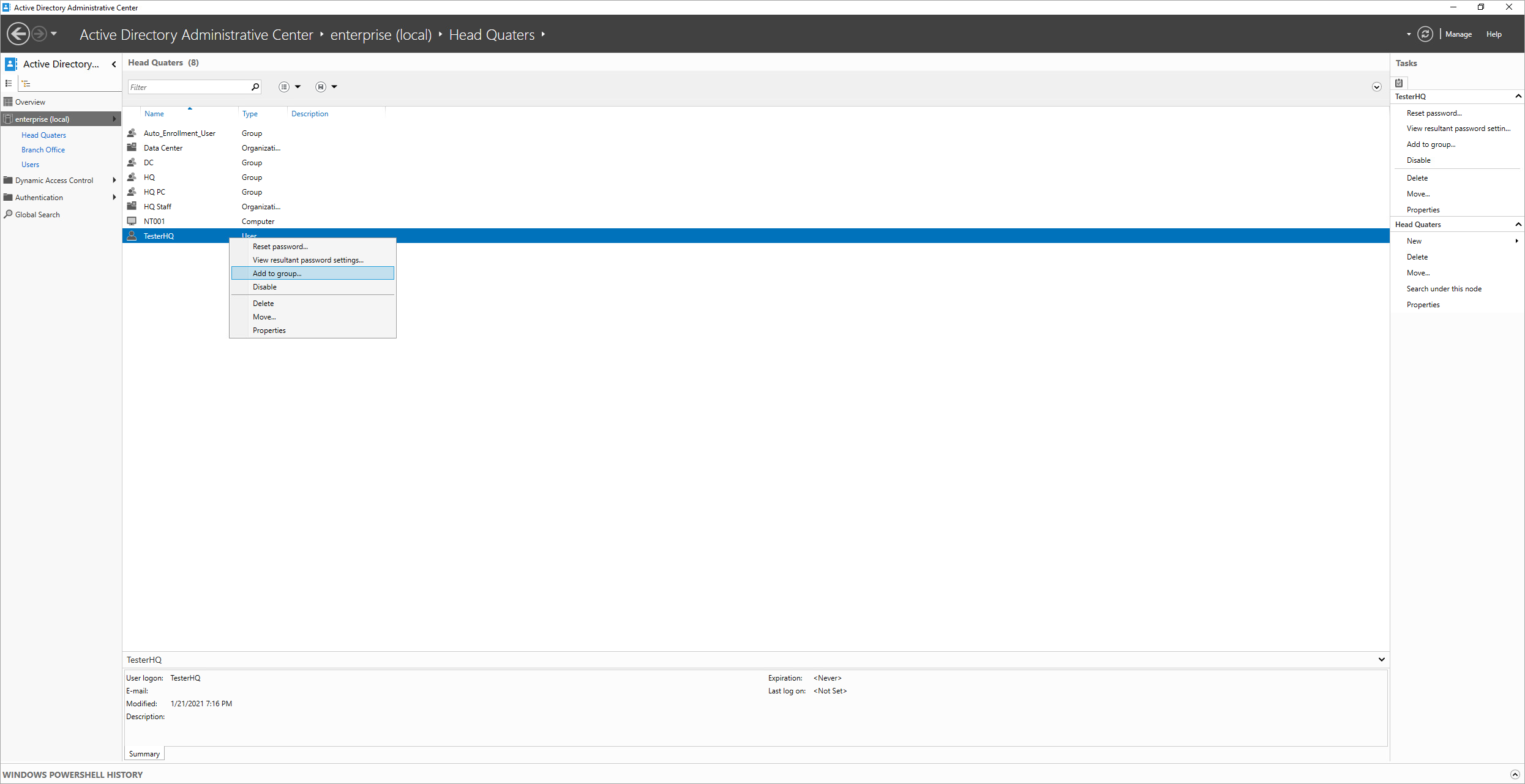
1.5. Enter the name of your created group in 1.3. Confirm with OK.
1.6. Now close AD AC.
1.7. Open Certificate Authority on the AD CS managed server (Server Manager > Tools > Certificate Authority).
1.8. Right click on the Certificate Templates and next select Manage.
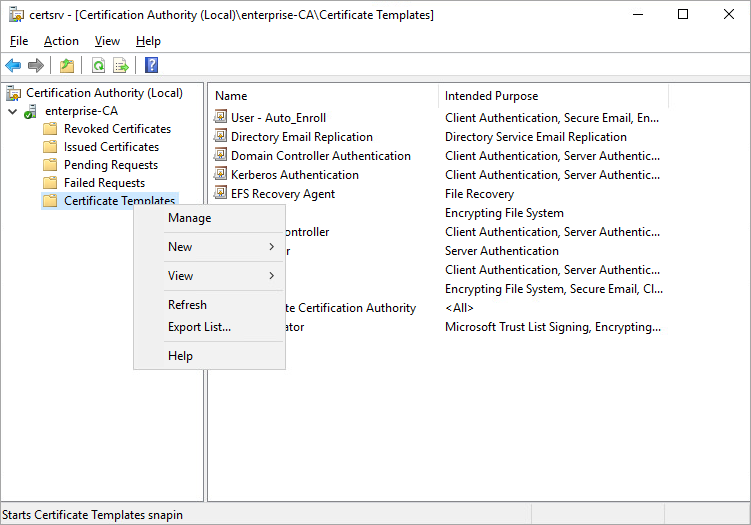
1.9. The certificate templates should appear in the panel on the right. Right click on the template named User and select Duplicate Template.
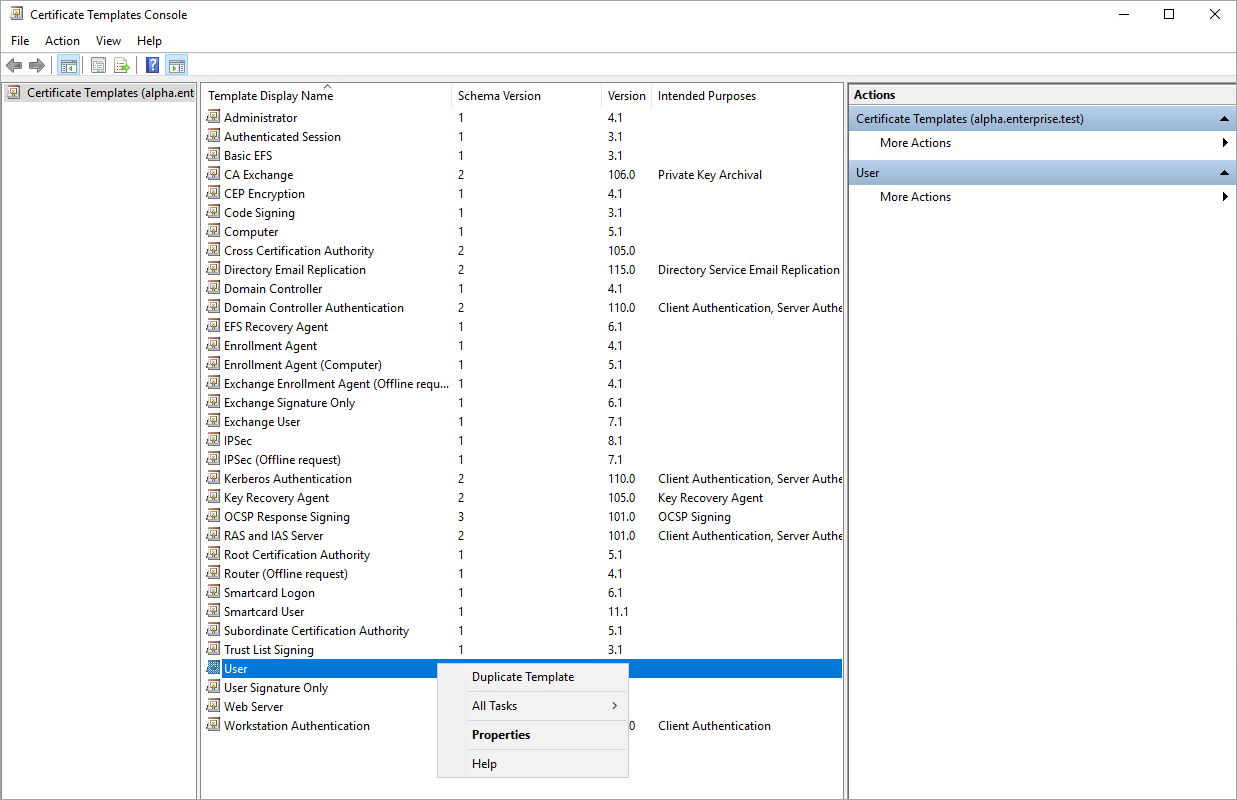
1.10. Make your changes to the tabs, following the recommendations below:
Compability: select the correct operating system for the certification authority and certificate recipient. This should be the lowest version of the operating system in your environment.
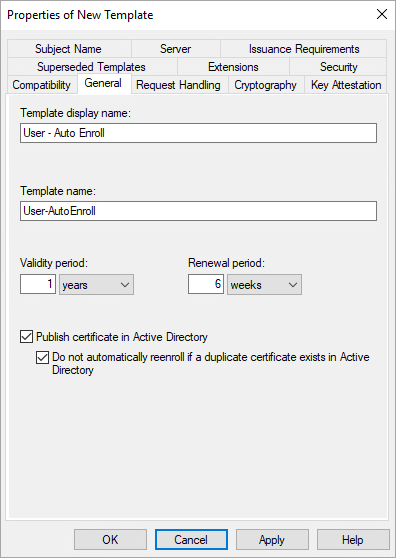
General: change the name (here: User - Auto Enroll) and set the validity period according to the organization policies (we recommend renewing no more than once a year). Then tick the option: Publish certificate in Active Directory and also: Do not automatically reenroll if a duplicate exists in Active Directory.
- Cryptography: recommended min. 2048 bit key, and 4096 for important groups.
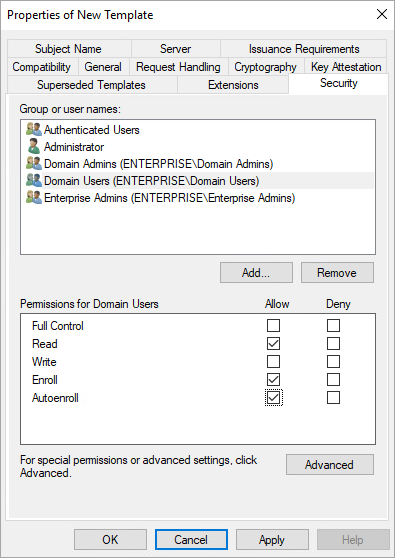
- Security: in Permissions for Domain Users section, tick the options as in the picture below.
Extensions- for Application Policies select: Client Authorization, and for Key Usage mark: Digital Signature and also: Signature is proof of origin.
Subject Name- mark the User principal name (UPN) option.
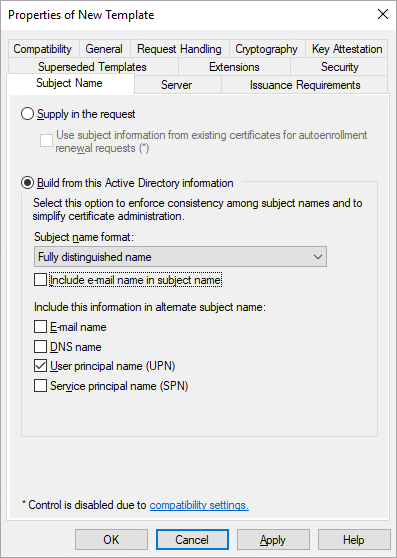
1.11. Leave the values in the other tabs as default. Confirm the changes with the OK button and close the certification template management panel.
1.12. Add your newly created template to the active templates. In order to do this, right-click on Certificate Templates and select New > Certificate Template to Issue.
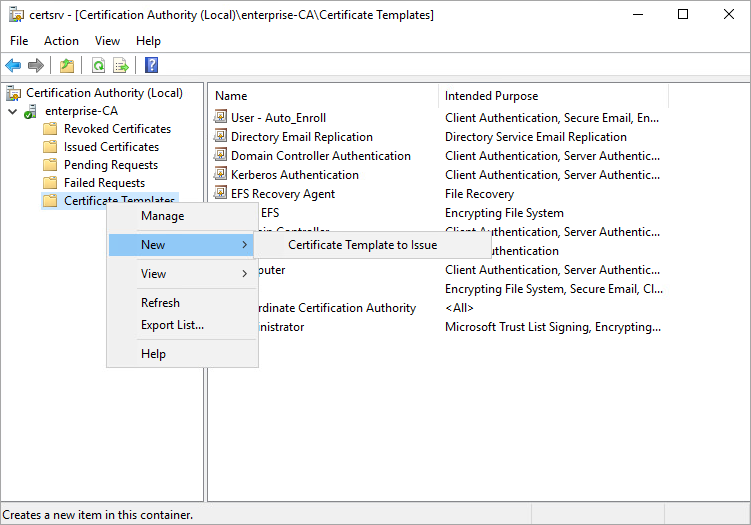
1.13. Now close Certificate Authority.
¶ 2. Device certificates
2.1. Repeat instructions: 1-6 from previous Step (The Users' certificate: from 1.1. to 1.6.), changing the group name for computers accordingly in 1.3., and in 1.4. - instead of adding users to the group: add selected devices to it.
2.2. Open the Certificate Authority on the AD CS manageable server (Server Manager > Tools > Certificate Authority).
2.3. Right-click on Certificate Templates and next select Manage.

2.4. In the panel on the right, your certificate templates should appear. Right click on the template named Computer and select Duplicate Template.
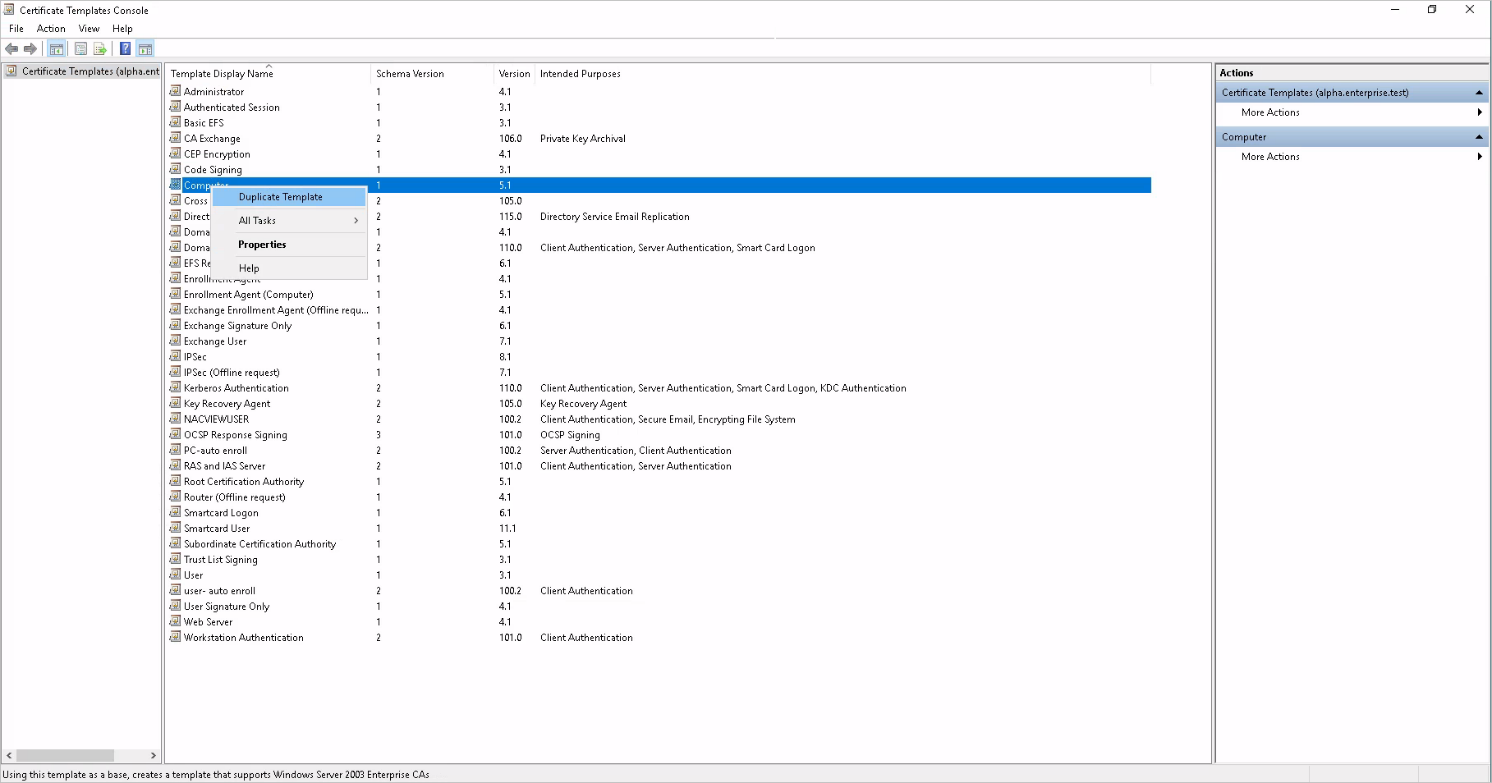
2.5. Make your changes to the tabs as follow:
Compability: select the correct operating system for the certification authority and certificate recipient. This should be the lowest version of the operating system in your environment.
General: change the name (here: User - Auto Enroll) and set the validity period according to the organization policies (we recommend renewing no more than once a year). Then tick the option: Publish certificate in Active Directory and also: Do not automatically reenroll if a duplicate exists in Active Directory.
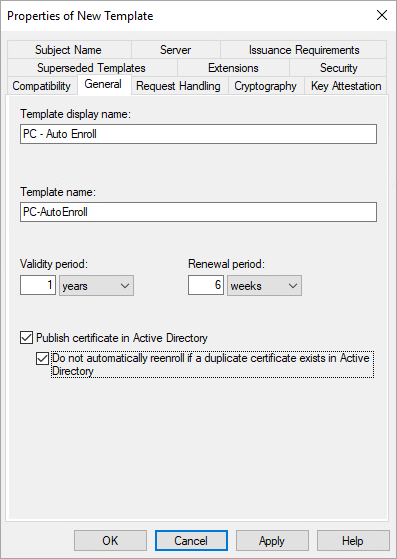
- Cryptography: recommended min. 2048 bit key, and 4096 for important groups.
- Security: in the Permissions for Domain Computers section, mark the options as shown in the picture below.
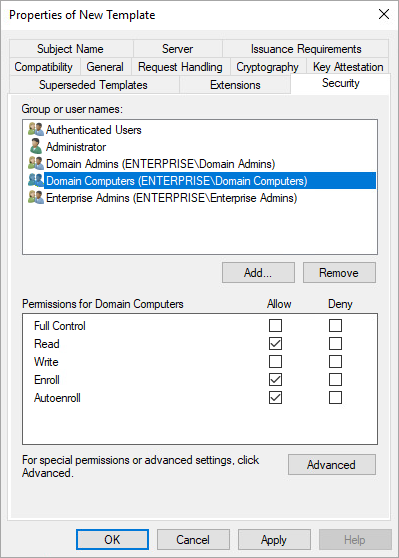
2.6. Leave the values in the other tabs as default. Confirm the changes with OK and close the certification template management panel.
2.7. Add the newly created template to active templates. To do this, right-click on Certificate Templates and select New > Certificate Template to Issue.
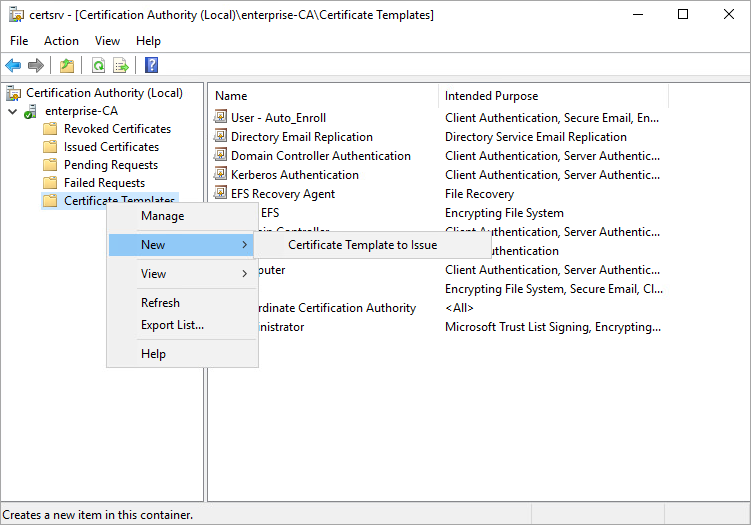
2.8. Close Certificate Authority.
¶ 3. Publication in GPO
3.1. On the domain controller, search and open Group Policy Management.
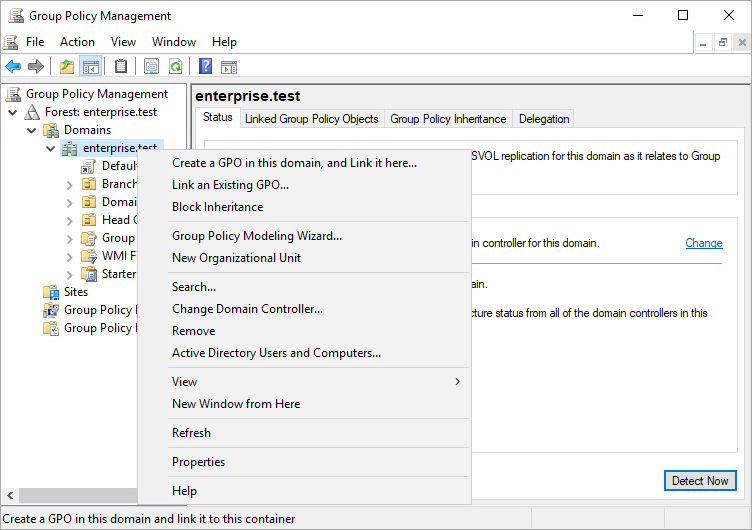
3.2. In the domain structure window, expand: Forest > Domains > selected domain.
3.3. Right-click on the selected domain and select: Create a GPO in this domain, and Link it here…
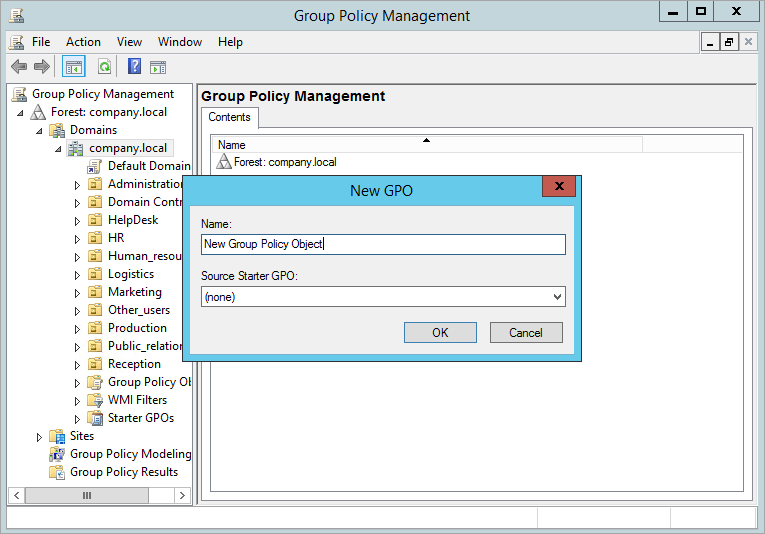
3.4. In the displayed window, enter a name for the new GPO and click OK.
3.5. Right click on the added GPO and select Edit.
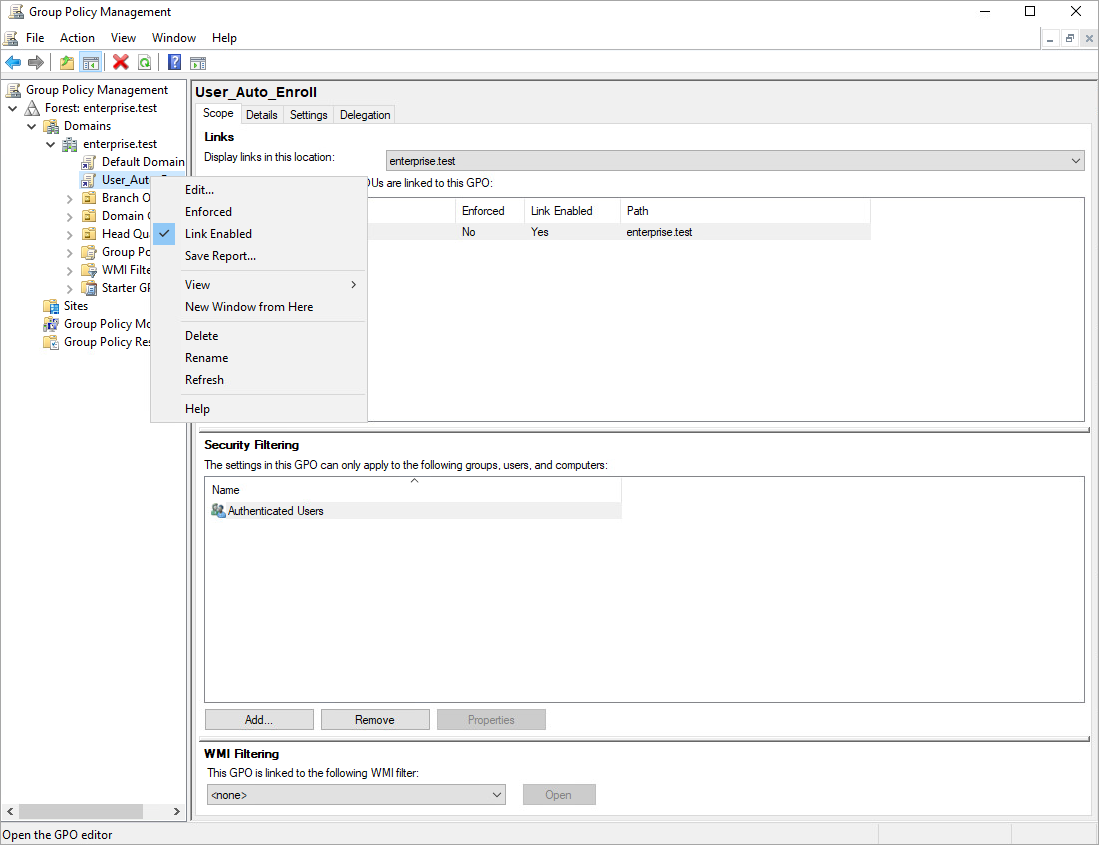
3.6. Go to: User Configuration > Policies > Windows Settings > Security Settings > Public Key Policies.
3.7. In the Object Type tab - select: Certificate Services Client - Auto-Enrollment. Set the values as the example below shows:
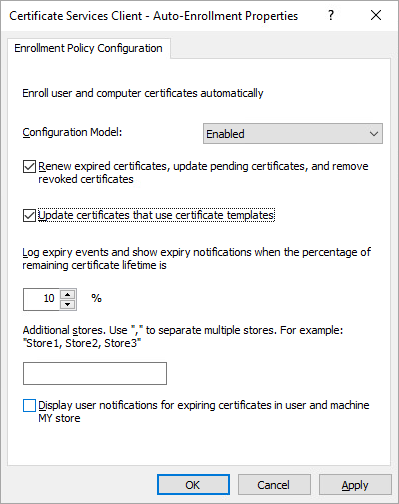
3.8. Confirm the changes with the OK button, then close the GPO Editor.
3.9. Go to the Scope tab of the newly created policy.
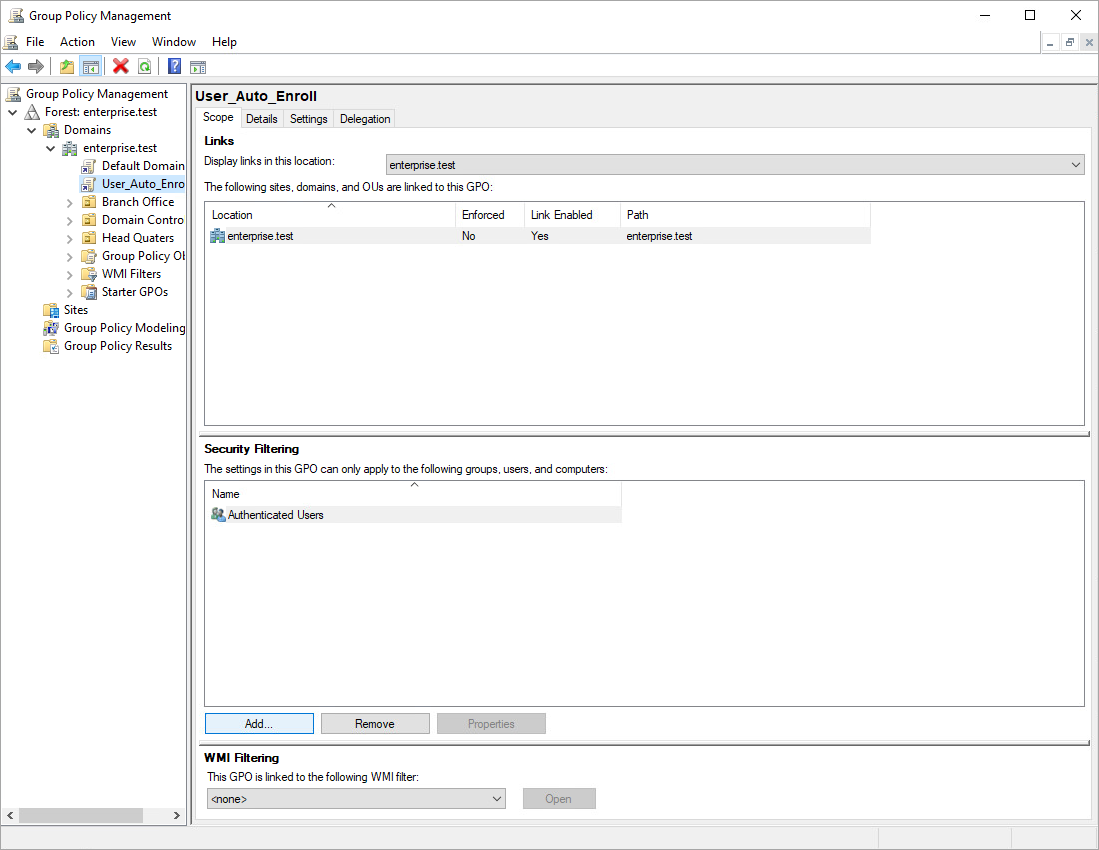
3.10. In the Security Filtering section: add the dedicated to users security group, which you created in step 1.
3.11. Confirm with OK and close it. Next time when you log in, the certificate should be automatically issued.
3.12. Repeat steps: 3.6- 3.11., opening Computer Configuration - instead of the User Configuration (step 3.6.) and also: selecting a security group dedicated to devices in the Security Filtering section (step 3.10.).