¶ Firewall Palo Alto API integration
¶ 1. Add an account with API access in Palo Alto
¶ 1.1 Creating an administrator profile
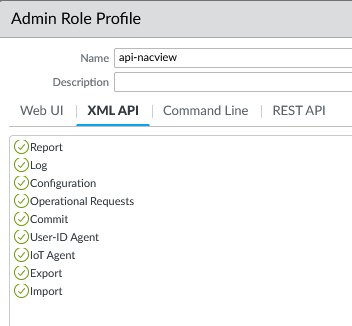
A new Administrator policy profile has been created on the Palo Alto device (Device -> Admin Roles tab) and access to XML API items has been allowed.
Name: api-nacview
¶ 1.2 Creating an administrator
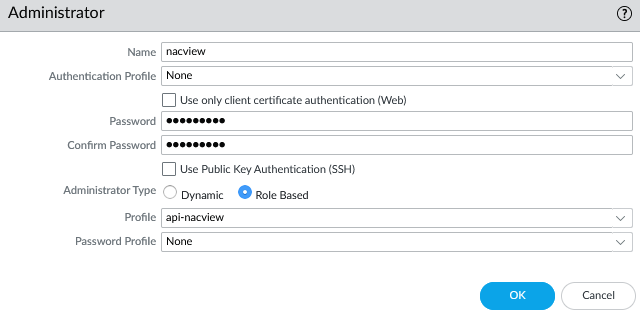
Under Device -> Administrators tab, a new administrator named nacview has been created, the administrator type is "Role Based", a password for the account has been provided, and the previously created profile has been assigned with API access named api-nacview.
¶ 1.3 Create a dynamic user group
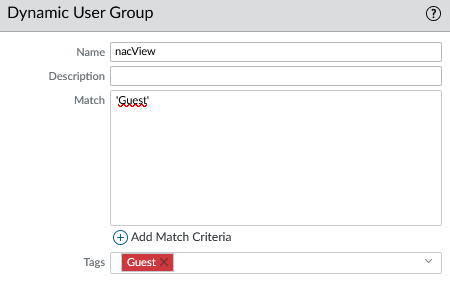
In tab Objects -> Dynamic User Groups a new group has been created to which people will be assigned by sending an API request from NACVIEW:
- Name: nacView
- Match: 'Guest'
- Tags: guest
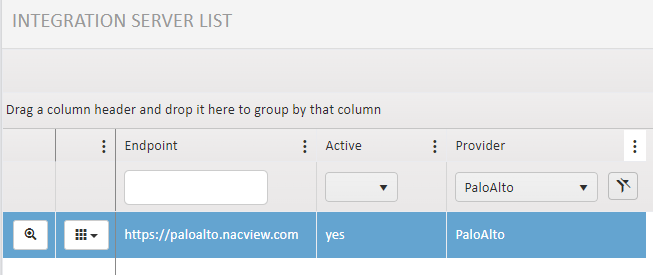
¶ 2. Configuring the integration server in NACVIEW
A Palo Alto integration server was configured in NACVIEW (Configuration -> Integration servers). The PaloAlto server was edited from the predefined list.
- Access point: https://192.168.8.110/api
- Login: nacview
- Password: nacview account password
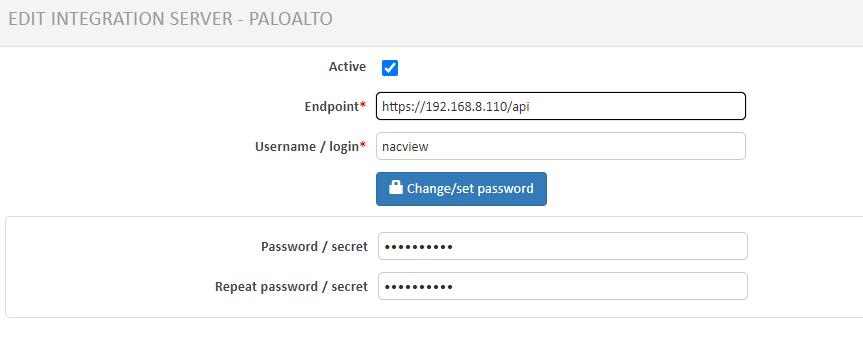
After entering the correct account details, a message should appear that the update is correct.
The integration server prepared in this way can then be used in the access policy.
If necessary, you can test the integration server before it is used in the policy.
The built-in "Mini Postman" tool can be used for this purpose. You need to double-click the configured integration server, then select "Test Service" and complete the parameters according to the requirements of the device.
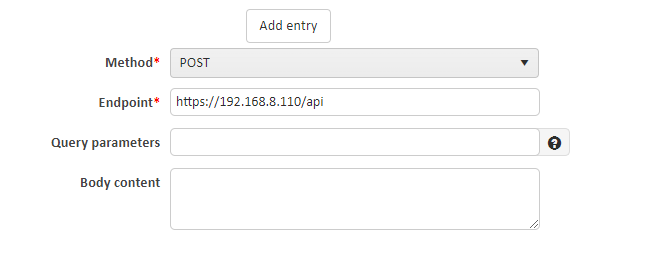
¶ 3. Access policy configuration in NACVIEW
An access policy allows an API request to be sent to the Palo Alto firewall when an end client accesses the network (Accounting-Start), and also when disconnected from the network (Accounting-Stop).
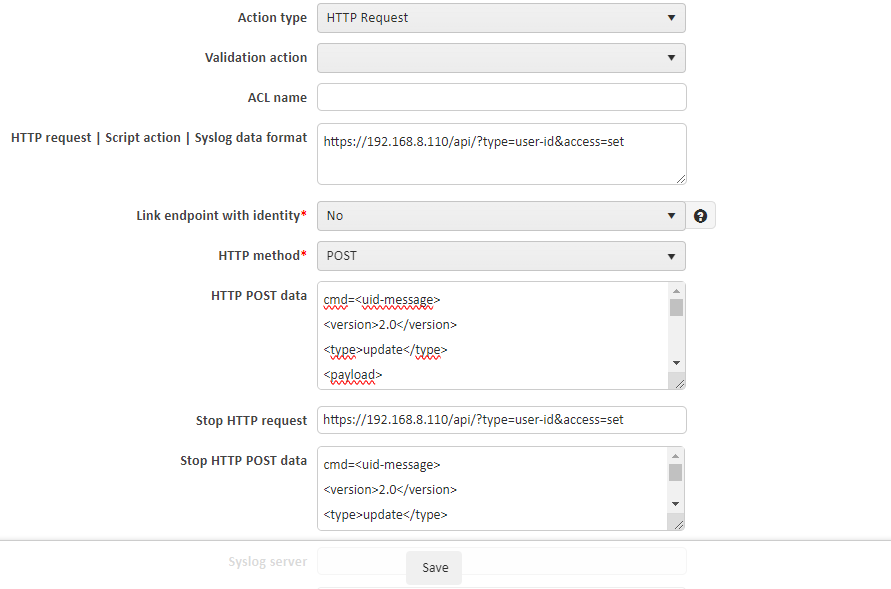
Go to NACVIEW GUI: Configuration -> Access policies and Select the policy to return the API request during client authentication, click Details -> Response action. Complete form, Save and Install list
The API request assigns the user to a dynamic nacView group based on the Guest tag.
- Action type: HTTP Request
- HTTP Request: https://192.168.8.110/api/?type=user-id&access=set
- HTTP Type: POST
- HTTP POST data:
cmd=<uid-message>
<version>2.0</version>
<type>update</type>
<payload>
<register-user>
<entry user="#LOGIN#">
<tag>
<member>Guest</member>
</tag>
</entry>
</register-user>
<login>
<entry name="#LOGIN#" ip="#IP#"/>
</login>
<register>
<entry ip="#IP#">
<tag>
<member>Guest</member>
</tag>
</entry>
</register>
</payload>
</uid-message></uid-message>
- Stop HTTP request: https://192.168.8.110/api/?type=user-id&access=set
- Stop HTTP POST data:
cmd=<uid-message>
<version>2.0</version>
<type>update</type>
<payload>
<unregister-user>
<entry user="#LOGIN#">
</entry>
</unregister-user>
</payload>
</uid-message>
- Integration server: PaloAlto