¶ FortiGate-50E
¶ Firmware Version
Version: FortiGate-50E v6.2.15,build1378,230605 (GA)
¶ Preliminary assumptions
For requirements of this document the following network infrastructure values have been assumed:
- NACVIEW IP server address: NACVIEW_SERV
- RADIUS communication key: RADIUS_KEY
- RADIUS server name: NV_RADIUS
- RADIUS accounting server ID: NV_ACC_ID
- RADIUS user group name: RADIUS_GROUP
- TACACS+ server name: NV_TACACS
- TACACS+ user group name: TACACS_GROUP
- Communication key for TACACS+ server: TAC+_KEY
- Fortiswitch Security policy name: 802.1x_POLICY
- Managed switch name or IP address: MANAGED_SWITCH
- SNMP v2c password: SNMP_SECRET
- SNMP v3 password: SNMP_AUTH, SNMP_PRIV
- SNMP user: SNMP_USER
- SNMP group: SNMP_GROUP
¶ RADIUS
config user radius
edit NV_RADIUS
set status enable
set server NACVIEW_SERV
set secret RADIUS_KEY
config accounting-server
edit NV_ACC_ID
set status enable
set server NACVIEW_SERV
set secret RADIUS_KEY
end
set acct-interim-interval 3600
end
The Radius server must send the attribute “Acct-Interim-Interval=xxx” (seconds) in the access accept message. Add post auth attribute in access policy.
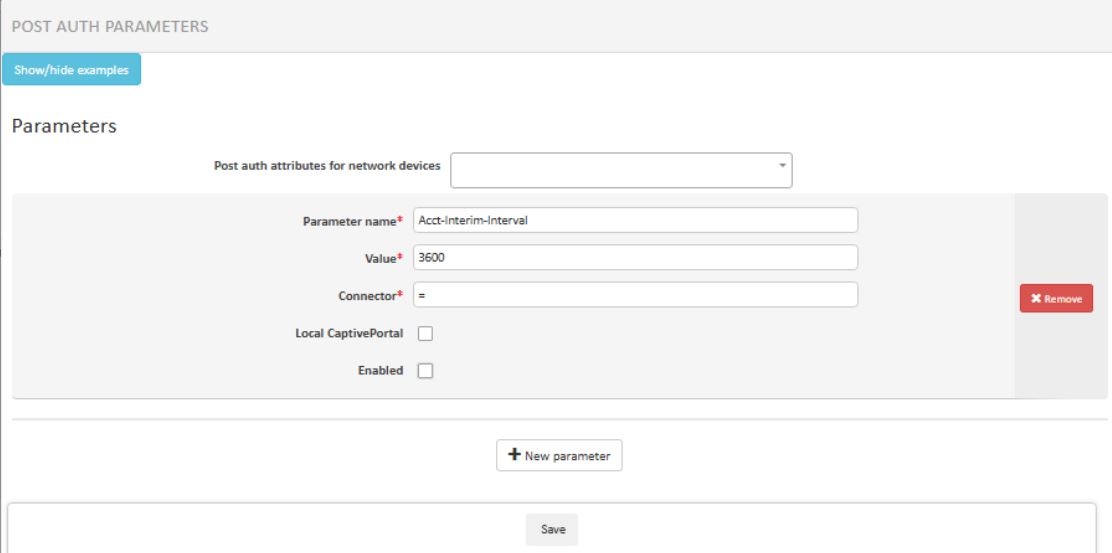
config user group
edit RADIUS_GROUP
set group-type firewall
set member NV_RADIUS
end
RADIUS Integration with FortiLink-Managed Switches
To ensure proper RADIUS server functionality with switches managed by FortiLink, create a firewall policy that permits traffic between the switches and NACVIEW servers.
Disable the NAT option in the firewall policy. When NAT is enabled, all network connection attempts from FortiSwitches will appear in NACVIEW as originating from the FortiGate IP address, preventing accurate device identification and authentication tracking.
¶ TACACS+
config user tacacs+
edit NV_TACACS
set server NACVIEW_SERV
set key TAC+_KEY
end
config user group
edit TACACS_GROUP
set group-type firewall
set member NV_TACACS
next
end
config system admin
edit TACACS-USER
set remote-auth enable
set accprofile super_admin
set vdom root
set wildcard enable
set remote-group TACACS_GROUP
next
end
config system global
set admin-restrict-local non-console-only
end
¶ Configuration of authorization
¶ Fortiswitch Security policy 802.1x
config switch-controller security-policy 802-1X
edit 802.1x_POLICY
set security-mode 802.1X-mac-based
set user-group RADIUS_GROUP
end
¶ Fortiswitch Security policy 802.1x + MAB
config switch-controller security-policy 802-1X
edit 802.1x_POLICY
set security-mode 802.1X-mac-based
set user-group RADIUS_GROUP
set mac-auth-bypass enable
end
¶ Apllying Fortiswitch Security policy on switch port
config switch-controller managed-switch
edit MANAGED_SWITCH
config ports
edit 1
set port-security-policy 802.1x_POLICY
¶ SNMP
¶ SNMP v3 (Recommended)
config system snmp sysinfo
set status enable
end
config system snmp user
edit SNMP_USER
set status enable
set trap-status enable
set queries enable
set notify-hosts NACVIEW_SERV
set security-level auth-priv
set auth-proto sha
set auth-pwd SNMP_AUTH
set prive-proto aes
set priv-pwd SNMP_PRIV
end
¶ SNMP v1/v2
config system snmp community
edit 1
set name SNMP_SECRET
set status enable
config hosts
edit 1
set ip NACVIEW_SERV
end
end
¶ Syslog
config log syslogd setting
set status enable
set server NACV_SERVER