¶ Cisco Meraki
¶ RADIUS
- Navigate to Wireless and Access control.
- Select the SSID you want to configure.
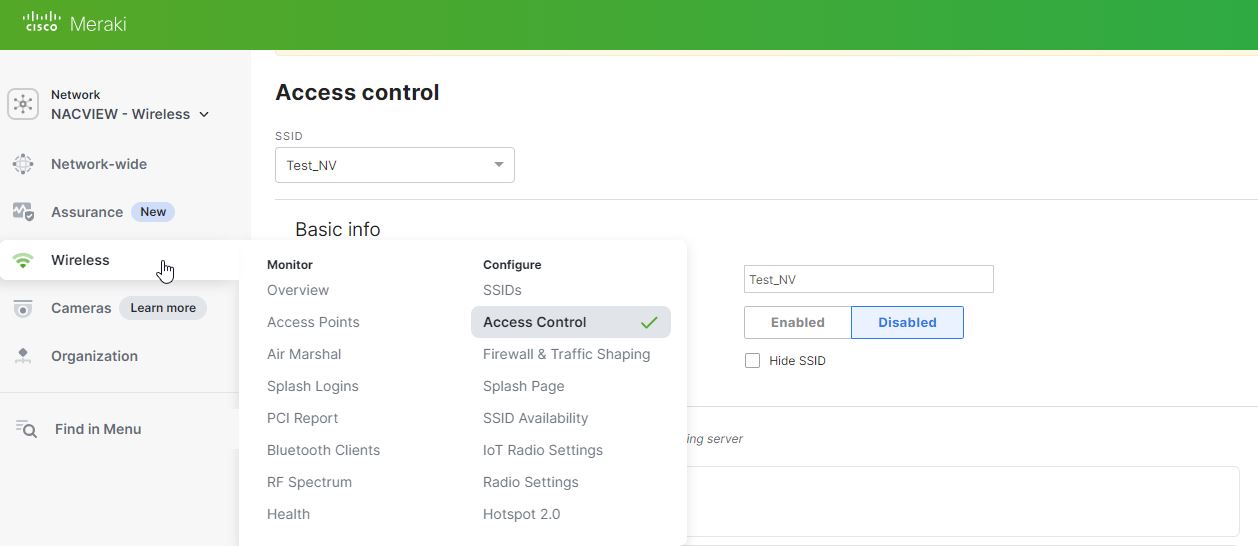
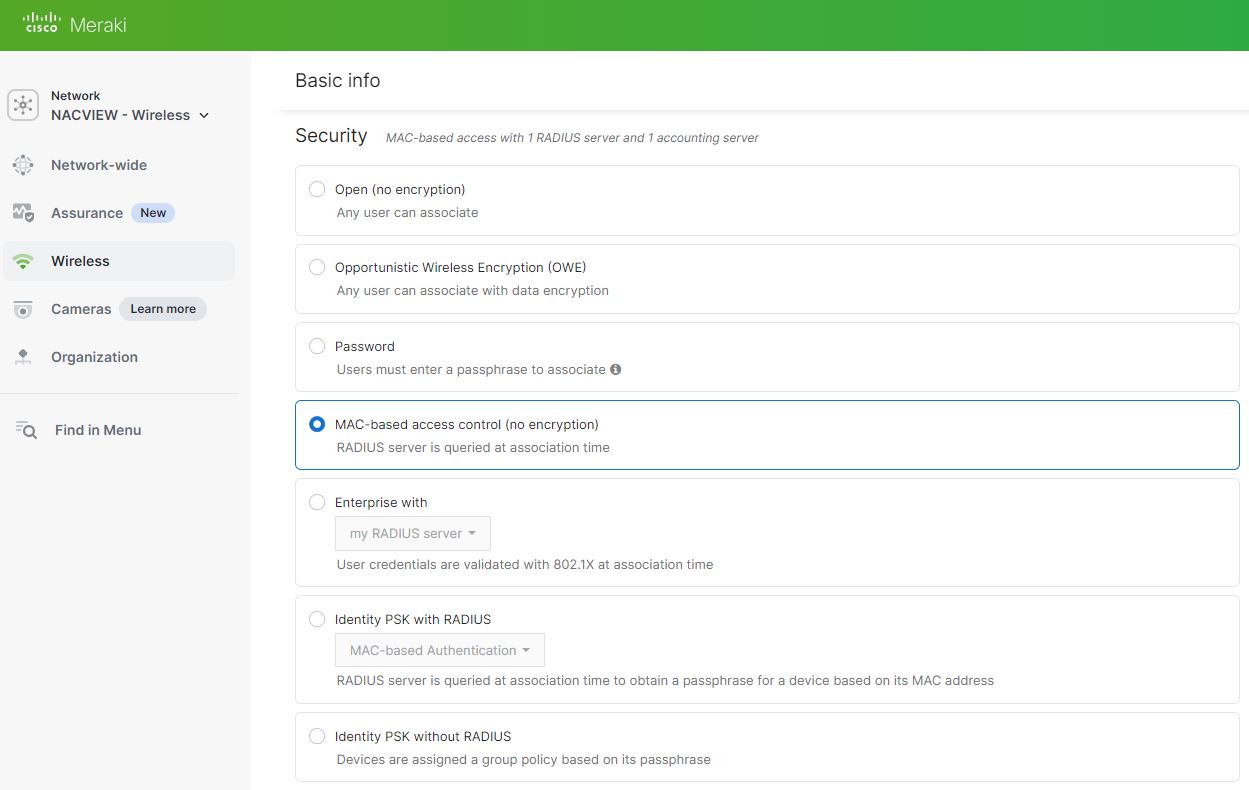
- In Scurity section, choose one of the following authentication methods
MAC-based access control – Authenticates client devices using their MAC addresses.
Enterprise with and my RADIUS server – Enables 802.1X authentication via a RADIUS server
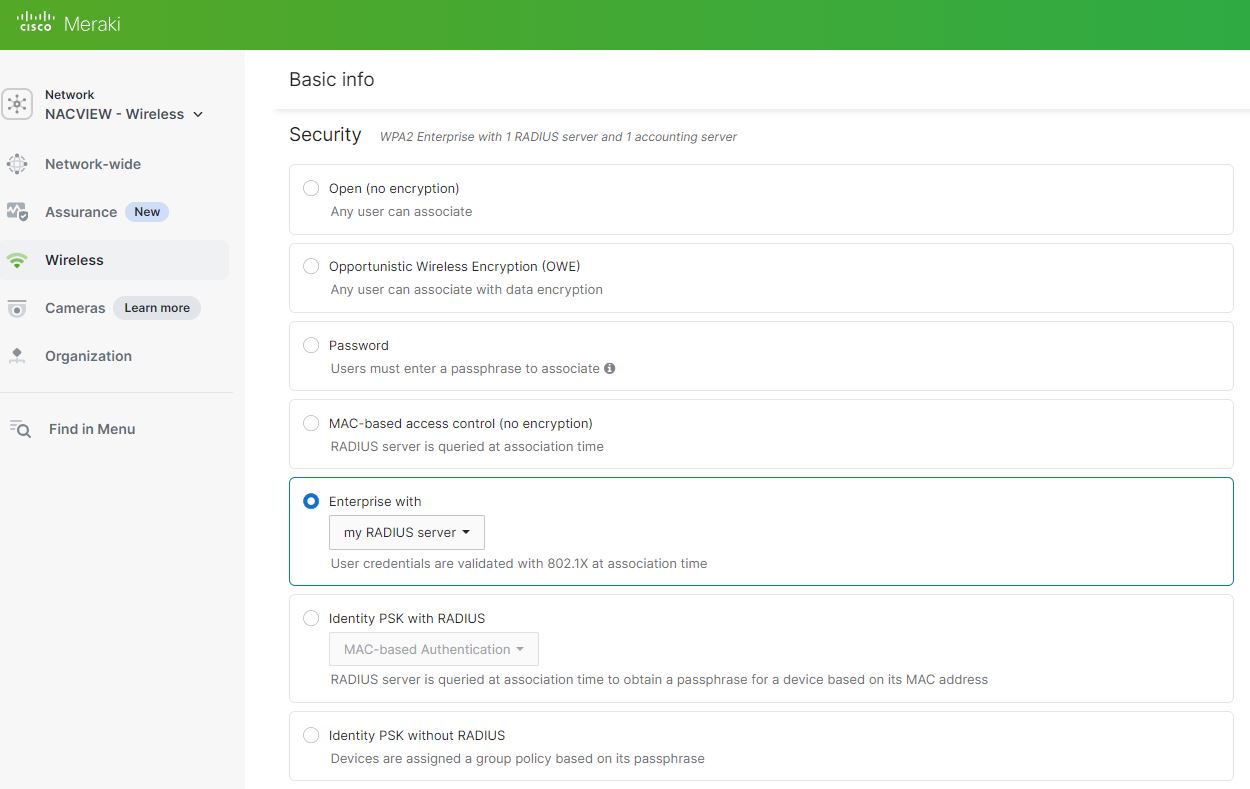
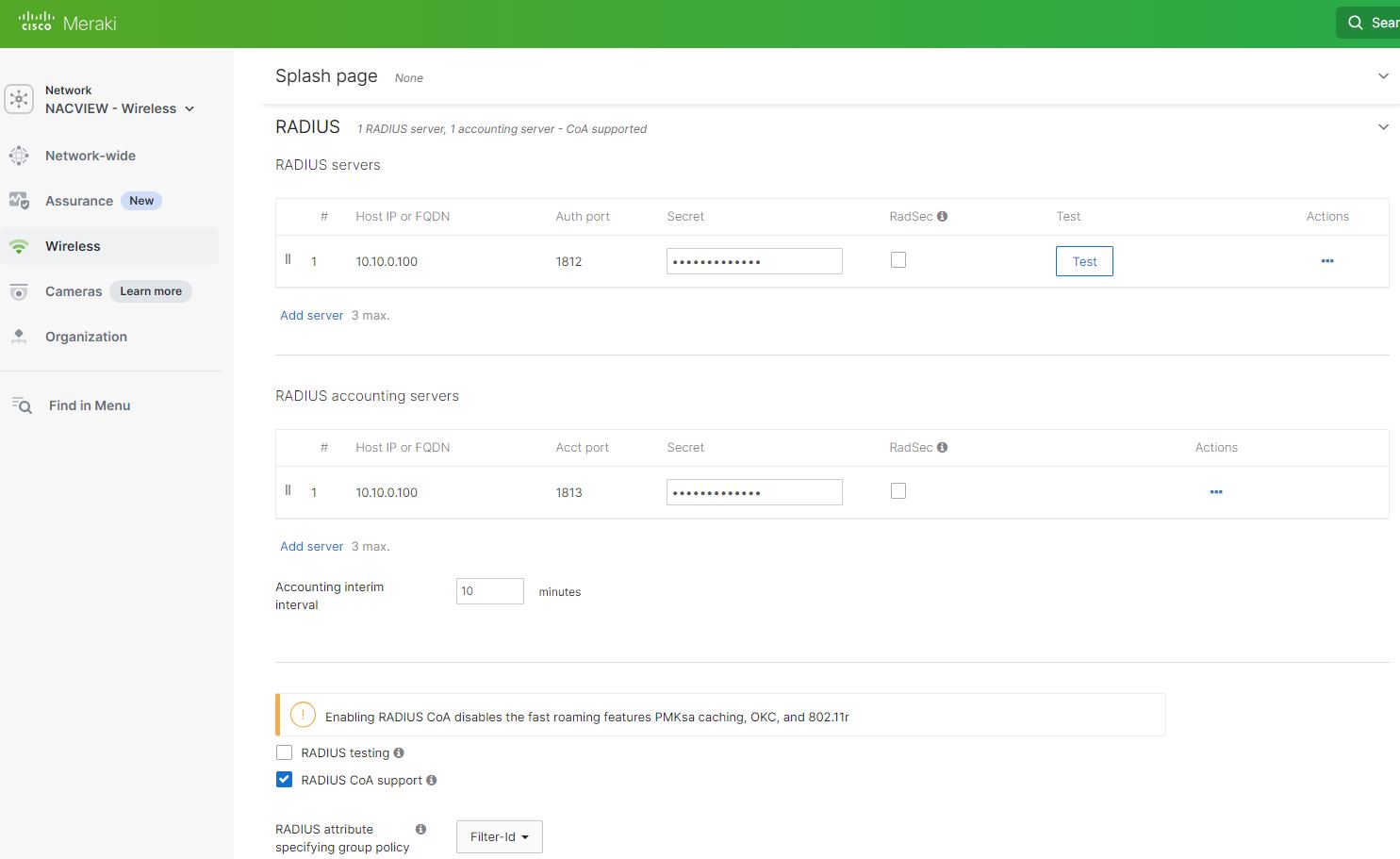
- In the RADIUS section, configure the NACVIEW server as follows:
RADIUS servers (Authentication): Enter the NACVIEW server's IP address, set the authentication port to 1812, and provide the shared key.
RADIUS Accounting servers: Enter the NACVIEW server's IP address, set the accounting port to 1813, and provide the shared key.
Enable RADIUS CoA support. Set the RADIUS Attribute to Filter-ID.
- In the Client IP and VLAN section select External DHCP server assigned option and enable Layer 3 Roaming.
Change RAIDUS Override to Override VLAN tag.
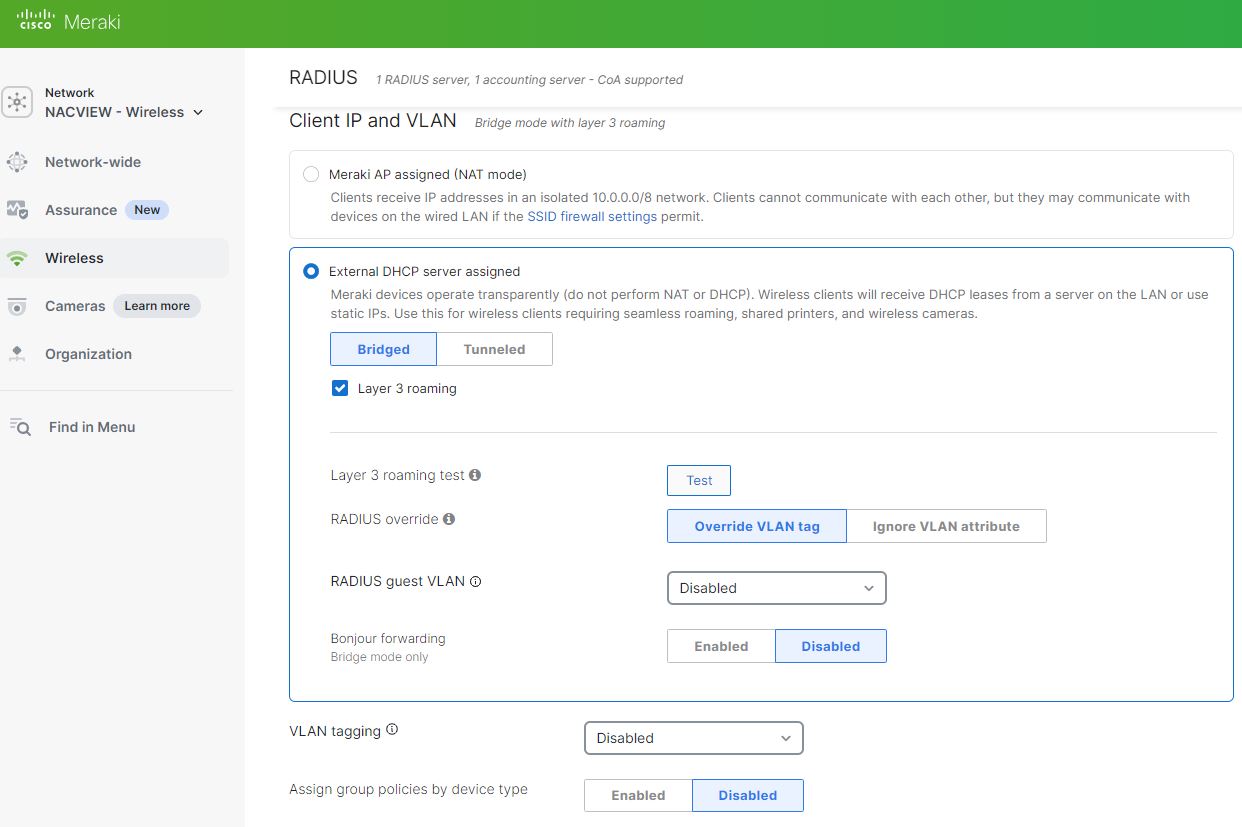
If using MAC-based Access Control, you can configure a guest VLAN for rejected clients or in cases where the RADIUS server is unreachable.
¶ SNMP
¶ SNMP v1/v2c
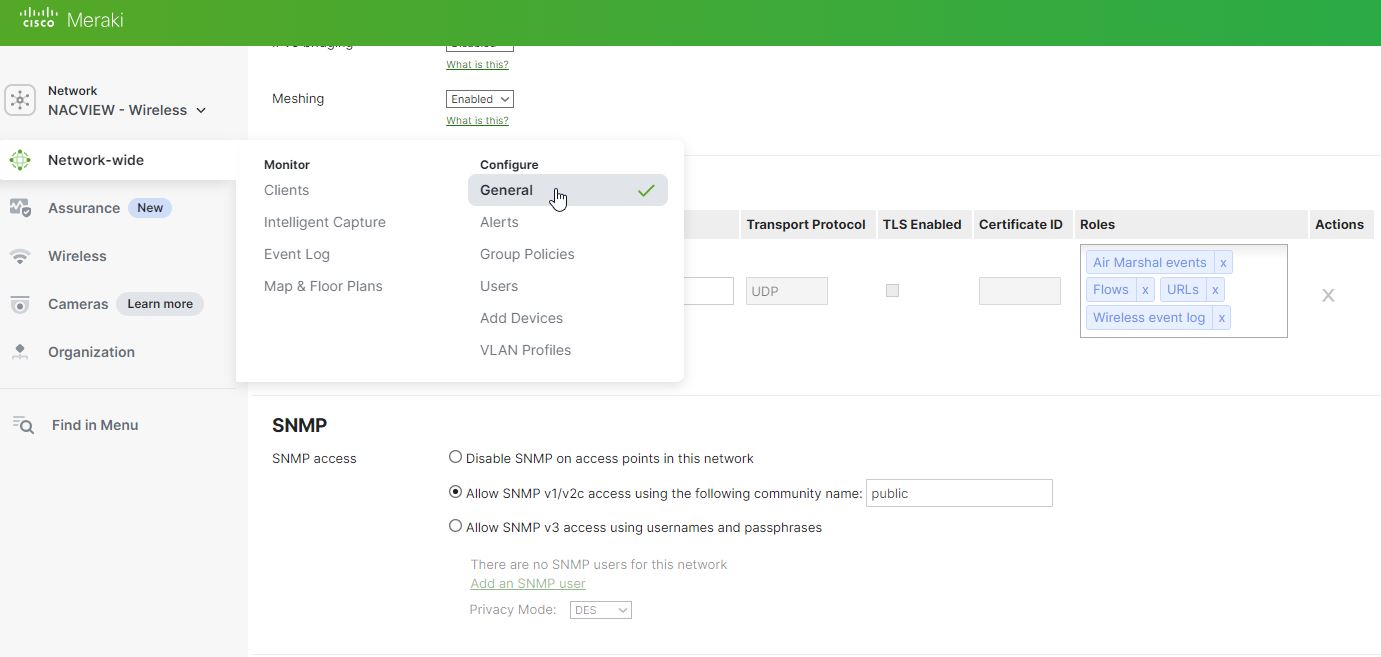
- Navigate to Network-wide and General
- In SNMP section choose SNMP v1/v2c option and provide community name.
¶ SNMPv3
- Navigate to Network-wide and General
- In SNMP section choose SNMP v3 option and click Add an SNMP user.
- Type the Username and Passprase.
- Privacy mode set as DES.
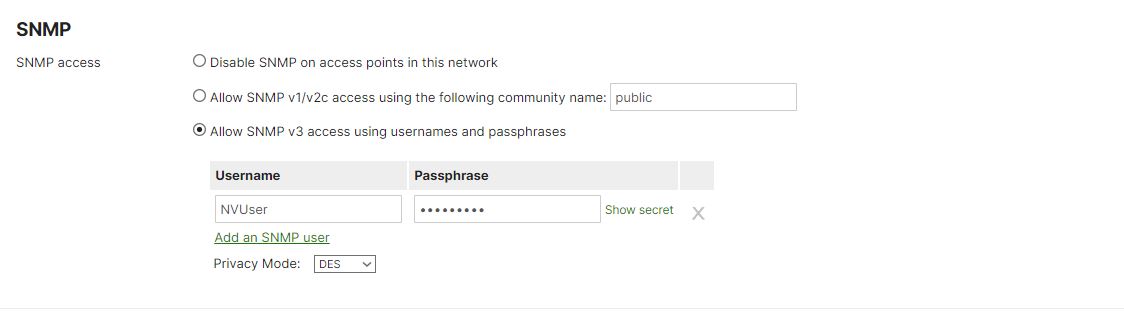
Authorization encryption is SHA by default. Passphrase for Authorization and Connection encryption is the same.
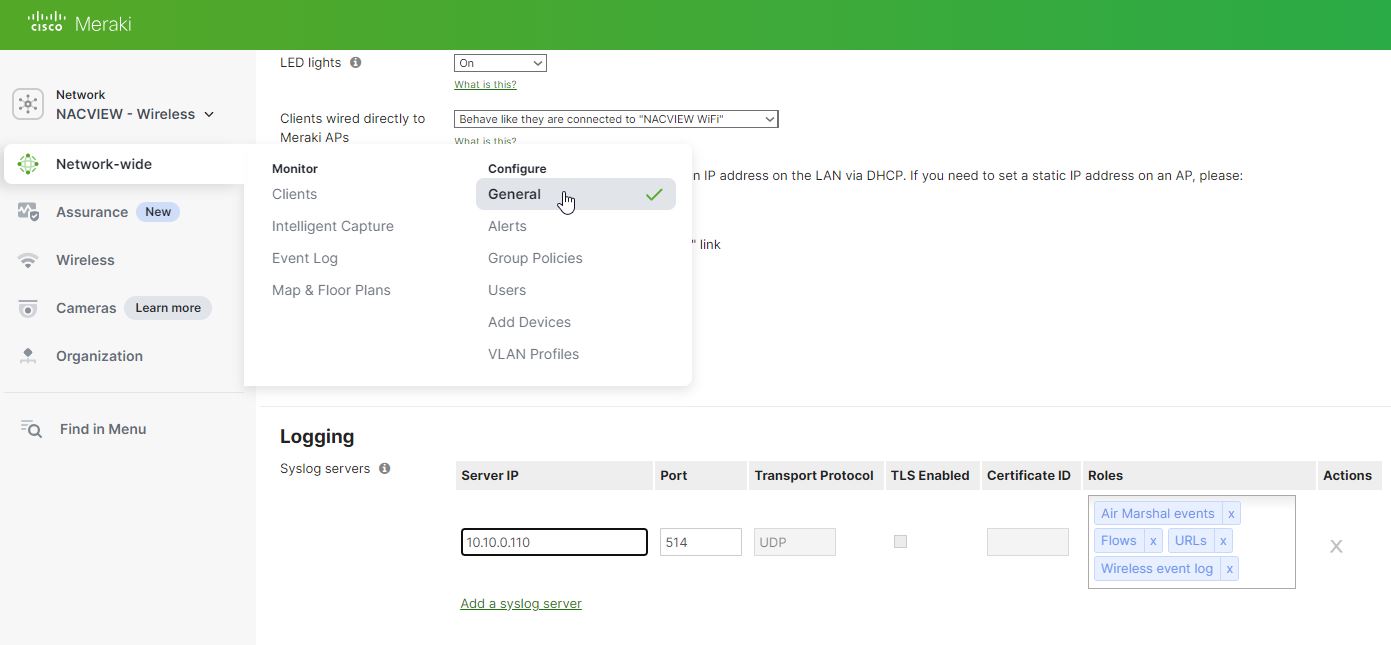
¶ SYSLOG
- Navigate to Network-wide and General.
- In Logging section click Add a syslog server.
- Type IP address of NACVIEW server. Leave port as a default 514 and choose desired Roles.
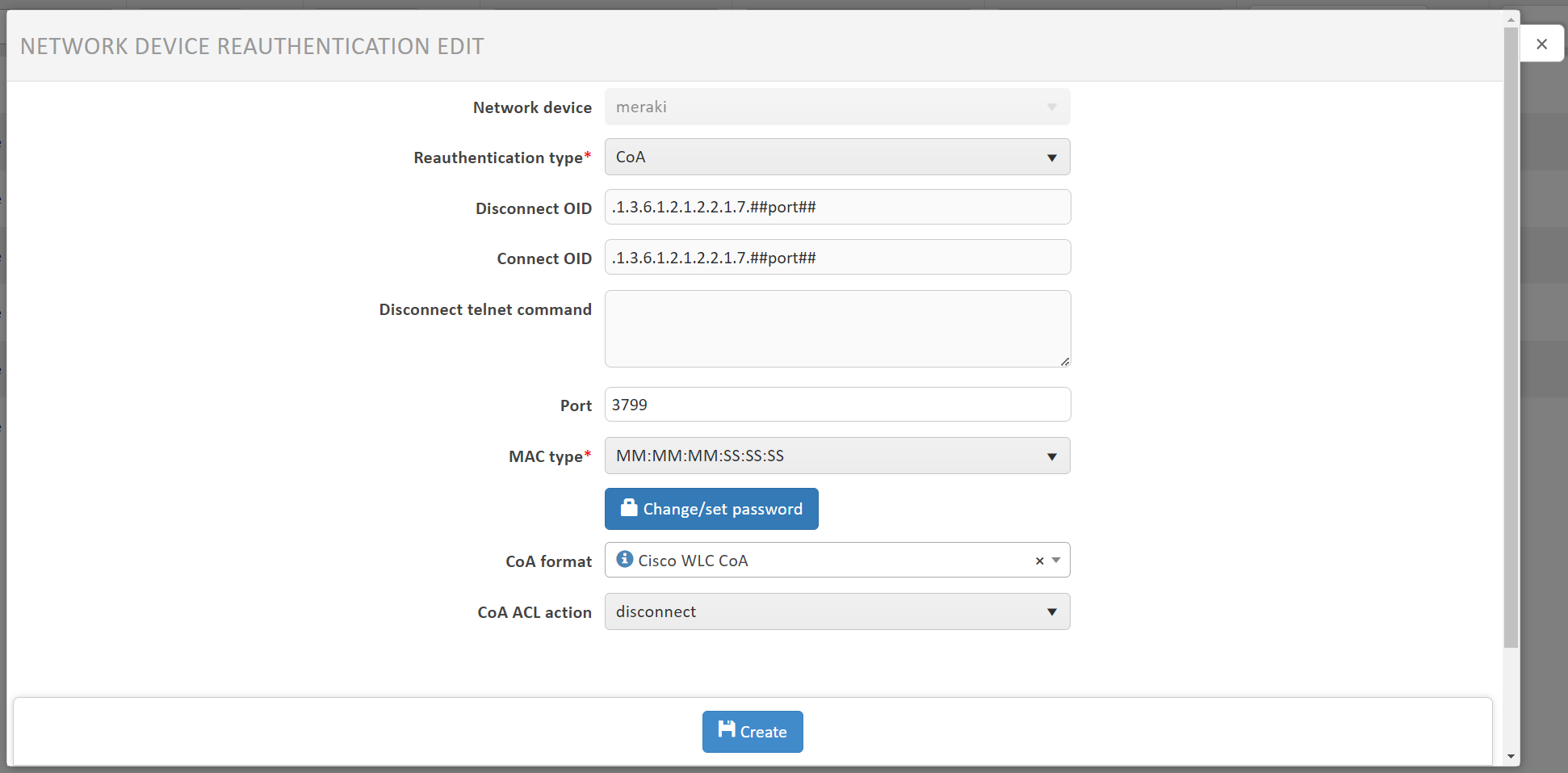
¶ CoA
If the Meraki has not yet been added to the list of network devices in NACVIEW, add it now. It is important to properly set the session disconnection mechanism after adding it. For this purpose:
I. Find the added Cisco Meraki device in the list and click on the button:
(in the same row).
II. In the preview window that opens on the right, expand the menu by clicking:
and then select: Reauthentication edit.
III. Complete the displayed form by selecting CoA as Reauthentication type and Cisco WLC CoA as CoA format.