¶ Cisco Catalyst C1000
Software: Cisco IOS Software, C1000 Software (C1000-UNIVERSALK9-M), Version 15.2(7)E1, RELEASE SOFTWARE (fc4)
¶ Preliminary assumptions
For requirements of this document the following network infrastructure values have been assumed:
- NACVIEW IP server address: NACVIEW_SERV
- RADIUS communication key: RADIUS_KEY
- Name of the server group for RADIUS protocol: RADIUS_GROUP
- IP switch address: SW_IP
- Switch management interface: MGMT_INT
- CoA password: (set in the authorization change settings) COA_SECRET
- SNMP v2c password: SNMP_SECRET
- SNMP v3 password: SNMP_AUTH, SNMP_PRIV
- SNMP user: SNMP_USER
- SNMP group: SNMP_GROUP
- Name of the server group for TACACS+ protocol: TAC+_GROUP
- Communication key for TACACS+ server: TAC+_KEY
¶ Configuration of connection with RADIUS server
C1000#configure terminal
C1000(config)#aaa new-model
C1000(config)#radius-server vsa send authentication
C1000(config)#radius-server vsa send accounting
C1000(config)#aaa group server radius RADIUS_GROUP
C1000(config-sg-radius)#server-private NACVIEW_SERV auth-port 1812 acct-port 1813 key RADIUS_KEY
C1000(config-sg-radius)#ip radius source-interface MGMT_INT
C1000(config-sg-radius)#exit
C1000(config)#aaa authentication dot1x default group RADIUS_GROUP
C1000(config)#aaa accounting dot1x default start-stop group RADIUS_GROUP
C1000(config)#aaa authorization network default group RADIUS_GROUP
C1000(config)#dot1x system-auth-control
¶ Change of Authority (CoA)
C1000#configure terminal
C1000(config)#aaa server radius dynamic-author
C1000(config-locsvr-da-radius)#client NACVIEW_SERV
C1000(config-locsvr-da-radius)#server-key COA_SECRET
C1000(config-locsvr-da-radius)#port 3799
¶ Configuration of authorization
¶ 802.1x protocol
C1000#configure terminal
C1000(config)#interface gigabitEthernet 0/1
C1000(config-if)#spanning-tree portfast edge
C1000(config-if)#switchport mode access
C1000(config-if)#dot1x pae authenticator
C1000(config-if)#authentication port-control auto
C1000(config-if)#authentication host-mode single-host
C1000(config-if)#authentication periodic
C1000(config-if)#authentication violation replace
C1000(config-if)#authentication order dot1x
C1000(config-if)#authentication priority dot1x
¶ 802.1x + fall-back for MAC address authorization
C1000#configure terminal
C1000(config)#interface gigabitEthernet 0/1
C1000(config-if)#spanning-tree portfast edge
C1000(config-if)#switchport mode access
C1000(config-if)#dot1x pae authenticator
C1000(config-if)#authentication port-control auto
C1000(config-if)#authentication host-mode single-host
C1000(config-if)#authentication periodic
C1000(config-if)#authentication violation replace
C1000(config-if)#mab eap
C1000(config-if)#authentication order dot1x mab
C1000(config-if)authentication priority dot1x mab
¶ MAC address authorization + fall-back for 802.1x
C1000#configure terminal
C1000(config)#interface gigabitEthernet 0/1
C1000(config-if)#spanning-tree portfast edge
C1000(config-if)#switchport mode access
C1000(config-if)#dot1x pae authenticator
C1000(config-if)#authentication port-control auto
C1000(config-if)#authentication host-mode single-host
C1000(config-if)#authentication periodic
C1000(config-if)#authentication violation replace
C1000(config-if)#mab eap
C1000(config-if)#authentication order mab dot1x
C1000(config-if)authentication priority mab dot1x
¶ MAB authorization
C1000#configure terminal
C1000(config)#interface gigabitEthernet 0/1
C1000(config-if)#spanning-tree portfast edge
C1000(config-if)#switchport mode access
C1000(config-if)#authentication port-control auto
C1000(config-if)#authentication host-mode single-host
C1000(config-if)#authentication periodic
C1000(config-if)#authentication violation shutdown
C1000(config-if)#mab eap
C1000(config-if)#authentication order mab
C1000(config-if)authentication priority mab
¶ 802.1x + fall-back for MAC address authorization (multi-domain mode)
C1000#configure terminal
C1000(config)#interface gigabitEthernet 0/1
C1000(config-if)#spanning-tree portfast edge
C1000(config-if)#switchport mode access
C1000(config-if)#dot1x pae authenticator
C1000(config-if)#authentication port-control auto
C1000(config-if)#authentication host-mode multi-domain
C1000(config-if)#authentication periodic
C1000(config-if)#authentication violation replace
C1000(config-if)#mab eap
C1000(config-if)#authentication order dot1x mab
C1000(config-if)authentication priority dot1x mab
¶ 802.1x + fall-back for MAC address authorization (multi-host mode)
C1000#configure terminal
C1000(config)#interface gigabitEthernet 0/1
C1000(config-if)#spanning-tree portfast edge
C1000(config-if)#switchport mode access
C1000(config-if)#dot1x pae authenticator
C1000(config-if)#authentication port-control auto
C1000(config-if)#authentication host-mode multi-host
C1000(config-if)#authentication periodic
C1000(config-if)#authentication violation replace
C1000(config-if)#mab eap
C1000(config-if)#authentication order dot1x mab
C1000(config-if)authentication priority dot1x mab
¶ 802.1x + fall-back for MAC address authorization (multi-auth mode)
C1000#configure terminal
C1000(config)#interface gigabitEthernet 0/1
C1000(config-if)#spanning-tree portfast edge
C1000(config-if)#switchport mode access
C1000(config-if)#dot1x pae authenticator
C1000(config-if)#authentication port-control auto
C1000(config-if)#authentication host-mode multi-auth
C1000(config-if)#authentication periodic
C1000(config-if)#authentication violation replace
C1000(config-if)#mab eap
C1000(config-if)#authentication order dot1x mab
C1000(config-if)authentication priority dot1x mab
¶ VoIP phone authorization
¶ C1000
C1000#conf t
C1000(config)#interface GigabitEthernet <interface ID>
C1000(config-if)#switchport mode access
C1000(config-if)#switchport voice vlan <VLAN ID>
¶ NACVIEW
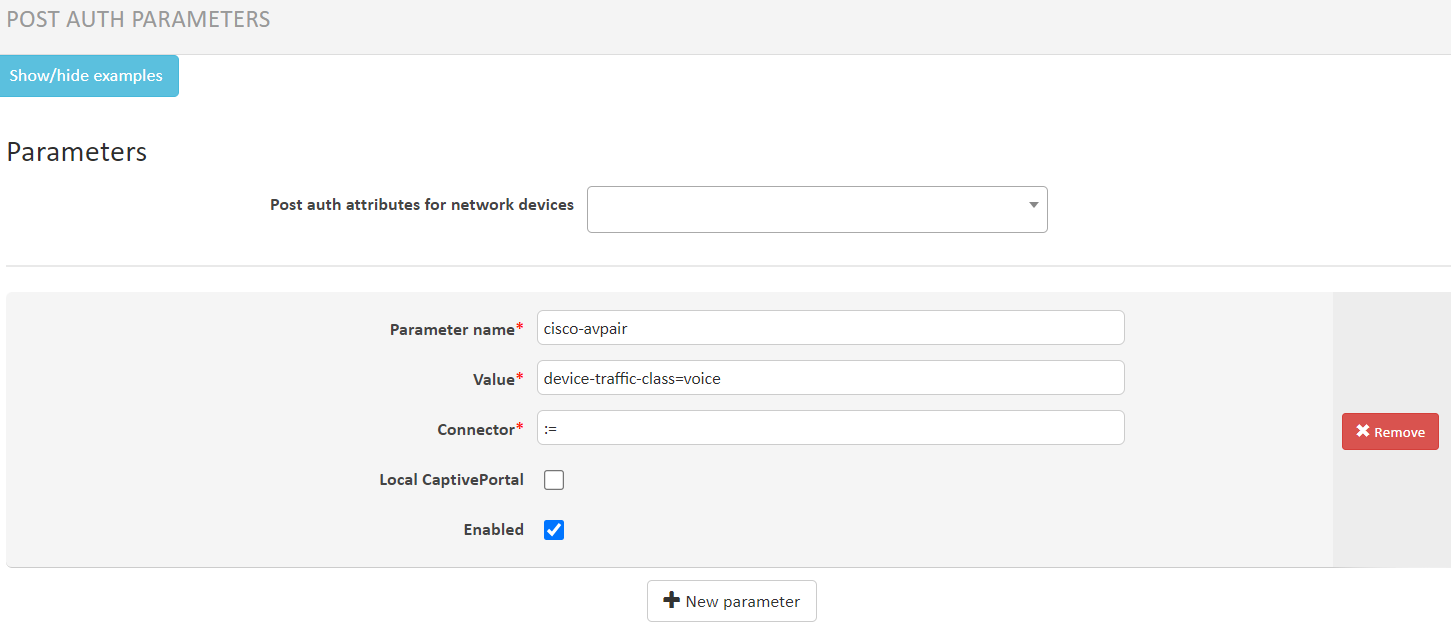
Attention! For the MAC access policy for authorization of VoIP phones, add the following Post auth attributes:
cisco-avpair := device-traffic-class=voice
See screenshot below:
¶ TACACS+ configuration
C1000(config)#aaa group server tacacs+ TAC+_GROUP local
C1000(config-sg-tacacs+)#server-private NACVIEW_SERV key TAC+_KEY
C1000(config-sg-tacacs+)#accounting acknowledge broadcast
C1000(config-sg-tacacs+)#ip tacacs source-interface MGMT_INT
C1000(config-sg-tacacs+)#exit
C1000(config)#aaa authentication login default group TAC+_GROUP
C1000(config)#aaa authorization exec default group TAC+_GROUP
C1000(config)#aaa accounting exec default start-stop group TAC+_GROUP
¶ SNMP
¶ SNMP v3 (recommended version)
C1000#configure terminal
C1000(config)#snmp-server enable traps
C1000(config)#snmp-server group SNMP_GROUP v3 priv context vlan- match prefix
C1000(config)#snmp-server ifindex persist
C1000(config)#snmp-server trap-source MGMT_INT
C1000(config)#snmp-server source-interface informs MGMT_INT
C1000(config)#snmp-server source-interface traps MGMT_INT
C1000(config)#snmp-server user SNMP_USER SNMP_GROUP v3 auth sha SNMP_AUTH priv des SNMP_PRIV
C1000(config)#snmp-server host NACVIEW_SERV inform version 3 priv SNMP_USER
C1000(config)#snmp-server host NACVIEW_SERV traps version 3 priv SNMP_USER
¶ SNMP v2c (version not recommended - ensuring the minimal safety level)
C1000#configure terminal
C1000(config)#snmp-server enable traps
C1000(config)#snmp-server ifindex persist
C1000(config)#snmp-server community SNMP_SECRET ro
C1000(config)#snmp-server trap-source MGMT_INT
C1000(config)#snmp-server source-interface informs MGMT_INT
C1000(config)#snmp-server source-interface traps MGMT_INT
C1000(config)#snmp-server host NACVIEW_SERV inform version 2c SNMP_SECRET
C1000(config)#snmp-server host NACVIEW_SERV traps version 2c SNMP_SECRET
¶ System logs redirection to NACVIEW server
C1000#configure terminal
C1000(config)#logging host NACVIEW_SERV
C1000(config)#logging source-interface MGMT_INT
C1000(config)#logging on
¶ MAC securities
Recommendations: switchport port-security can only be used on port in static access or trunk mode.
- To switch port-security mode (by default dynamic MAC addresses memorization):
C1000(config-if)#switchport port-security - To add static MAC address to the configuration:
C1000(config-if)#switchport port-security mac-address H.H.H - To add dynamic MAC addresses in sticky mode:
C1000(config-if)#switchport port-security mac-address sticky - To configure any forbidden address on given port:
C1000(config-if)#switchport port-security mac-address forbidden H.H.H
Default (dynamic) mode - is the mode in which the switch dynamically memorizes MAC addresses on port. They get removed from the address table after each link-down has appeared on port.
Static mode - is the mode in which the admin statically sets up to 4096 addresses. They being saved in the current device configuration. When the fixed amount of addresses is smaller than the maximum value determined, then the remaining MAC addresses are being registered in the dynamic or sticky mode.
Sticky mode - is the mode where the switch dynamically memorizes MAc addresses on port, and here they get saved as static addresses.
- Configuration of the port violation mode (detection of an unregistered MAC address in the static mode OR exceeding the maximum number of addresses in the dynamic mode OR detection a registered MAC address on any other port:
C1000(config-if)#switchport port-security violation [protect | restrict | shutdown]
Protect Mode- files are being rejected untill the port violation stops.
Restrict Mode- as the above**,** makes the SecurityViolation counter increase.
Shutdown Mode- sets the port in the error-disabled mode.
IMPORTANT! The above modes work equally as well with the command***
authentication violation
- To configure the maximum number of addresses on port, where X ranges from 1 to 4097:
C1000(config-if)#switchport port-security maximum X - To configure the maximum time to life of dynamic addresses, where X ranges from 1 to 1440 (in minutes):
C1000(config-if)#switchport port-security aging time X - To configure MAC addresses aging type (absolute, since it has been added to the (absolute) table OR based on inactivity of given address):
C1000(config-if)#switchport port-security aging type [ absolute | inactivity] - To switch the port aging for statically added addresses:
C1000(config-if) #switchport port-security aging static
¶ Auxiliary recommendations
- Current device configuration:
C1000#show running-config - Initial device configuration:
C1000#show startup-config - 802.1x Configuration:
C1000#show dot1x - Interface x configuration 802.1x:
C1000#show dot1x interface gigabitEthernet X/x details - RADIUS server configuration:
C1000#show radius server-group all - Interface x 802.1x statistics:
C1000#show dot1x interface gigabitEthernet X/x statistics - Authorization sessions present in the system: :
C1000#show authentication sessions - Details of authorization sessions on the given interface: :
C1000#show authentication sessions int g1/0/1 details - Authorization sessions using the given authorization method:
C1000#show authentication sessions method {dot1x, mab, webauth} - Current configuration copying on NACVIEW server:
C1000#copy running-config - Saved configuration copying on NACVIEW server:
C1000#copy startup-config - Configuration copying from NACVIEW server to the current configuration:
C1000#copy tftp://NACVIEW_SERV/CONF_FILE.txt running-config - Configuration copying from NACVIEW server to the initial config:
C1000#copy tftp://NACVIEW_SERV/ CONF_FILE.txt startup-config